Oracle Convergence: never-ending story of 0-day
…DARY!!! Finally, I can write about one of my findings, vendor fixed it. Some of you might be familiar with Oracle’s product called Convergence. It is a web application, part of Oracle Communications Messaging Server. According to wiki:
"Oracle's Messaging Server could potentially be the most widely deployed commercial
email server on the planet, with claims of 150 million mailboxes deployed worldwide
(mostly by ISPs, telcos, universities, government, and cable TV broadband providers)."
Quick search on Google for “Convergence webmail” shows there are few instances running around ;) Now imagine there was a Cross Site Scripting vulnerability in it… no big deal right? Little background about Convergence… almost everything is handled by JavaScript, so with XSS you can do whatever you want, send emails, add contacts, read emails etc. More interesting, right? What if this vulnerability was inside part which displays email message, so to get owned you only had to open malicious email? Now we talking :)
Ahh, one more thing, I have found 2 of these :)
Now, before you continue… I want to play a game with you… What do you think… How long it took for Oracle to fix these issues? Days? Months? So one of them around 5 months, and the second one around… hmmm… 15-16 months. Yes, they knew about it for at least 15 months… how long was it there… who knows.
Let the fun part begin.
Issue#1: Images bad! We protect!
This one has been found 2nd, but fixed as 1st (only 5 months). Email clients protect users by blocking images inside message. Sooo our message has a img inside:
<img src="blah"/>
“Hey Bob! How we gonna block these images in our webmail?”
“That’s super easy man, just replace all ‘src=*’with empty string”
Yes, you see it right. You are protected in 100% from nasty pictures and in addition you receive XSS! If you decide to enable images XSS goes away.
I won’t provide ready to use PoC, reason should be clear.
Interesting thing I’ve learnt about Oracle… if you are their customer (long story short, I’ve used my previous company’s account to contact them) and you report vuln in their app they will do 2 things:
- patch it quietly,
- don’t give you any credits at all.
Thank you Oracle, great work! In the end, they closed my ticket and fixed reported issue, yay!
Issue#2: Don’t rush mate… be coool!
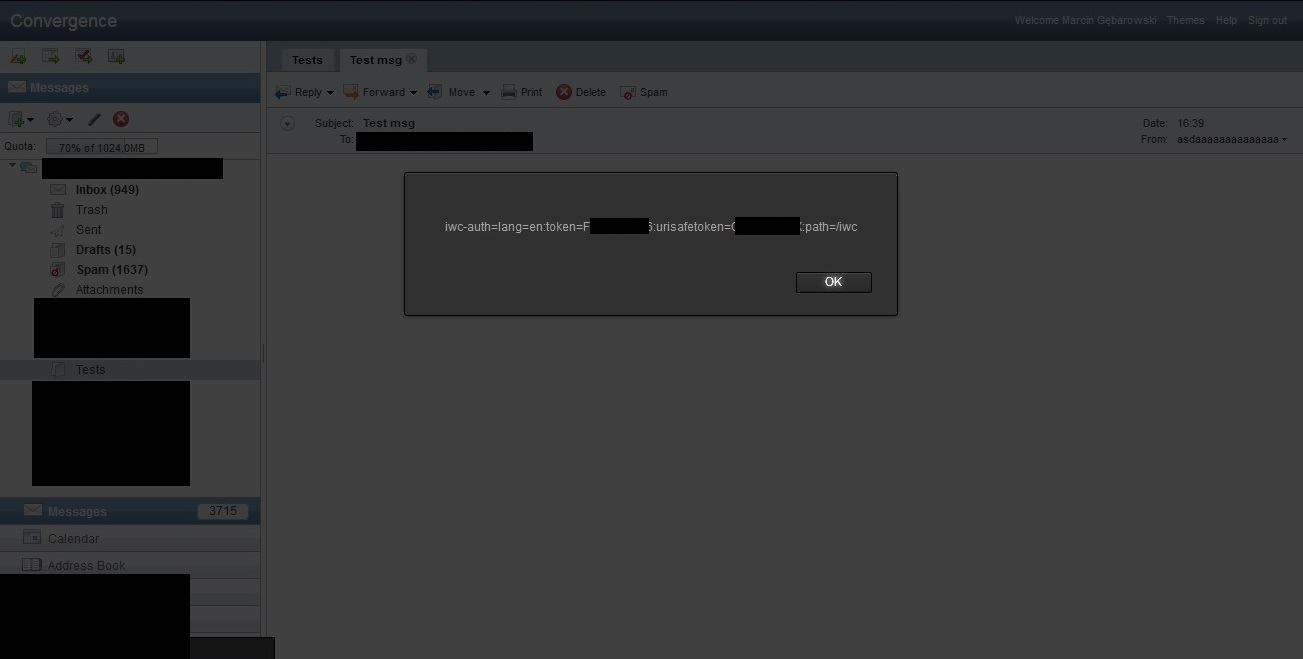
Now the 15 months one…btw to make things funnier, there was a workaround to stop this vulnerability, but I’m not aware of any comms from Oracle to their customers to apply it (#SuperHardCommandToChangeOneOption).
Every webmail client has to have proper XSS filters in place. JavaScript can add new “depth” to messages, but probably no one wants that kind of “depth”. There are different ways to sanitize message. I have no idea what had been used in Convergence, but based on the 1st issue I’d say “replace” FTW!
For some reasons they really didn’t like this string:
target="_top" href='data:javascript;base64,'
which properly placed (somewhere in the middle) would let an attacker inject any html tag into the message viewer :) To hide any sign of malicious message I had to inject an opening tag for comment too (browser will close this one for you).
So here’s my evil message waiting inside inbox:
Let’s view it:
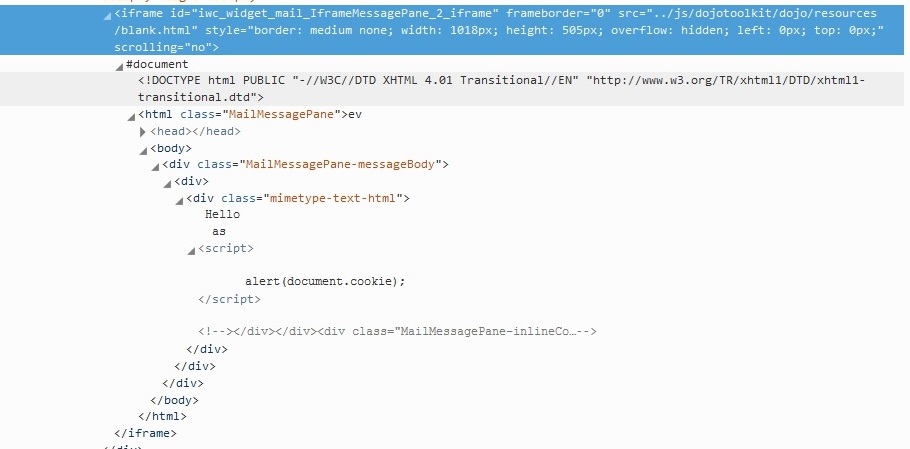
Here’s how this looks in code:
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 4.01 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html class="MailMessagePane"><head><link rel="stylesheet" type="text/css" href="../layout/css/mail/MessagePane.css?"></link></head><body><div class="MailMessagePane-messageBody"><div><div class="mimetype-text-html">Hello
as<script>
alert(document.cookie);
</script><!--
></div></div><div class="MailMessagePane-inlineContainer"></div></div></body></html>--></div>
Again, I won’t post how the payload should look, because I’m quite sure a lot of companies are still running vulnerable versions (one can still find instances vulnerable to stuff described here, lol).
I have just found CVE number of my issue (hopefully this one is mine, lol): CVE-2015-4793. Found it while googling for link to security patch release xD
This ends my story with Oracle… I have received a simple: “Issues reported by you have been fixed [….] Thank you” email. Also seen my name and surname in credits box in release notes. Yay!! Hopefully, I will never have to report anything in Oracle’s product again…